As the primary change manager for a client’s learning management system (LMS), I have gathered key information and considerations for anyone working in a similar role within a validated LMS environment. This is the first of two blog posts on the topic of validation.
What is different about a validated LMS environment?
For most companies looking to make a change in their learning management system, the process of doing so can be as simple as making the desired update in a test environment, testing to ensure it works, and then deploying the change into their live Production site. However, the process is much more in-depth in industries such as Healthcare and Life Sciences, where training compliance and data integrity are of tantamount importance so the systems in place must be carefully controlled and changes are vetted and approved. Organizations within these industries use validated LMS environments to manage data because there is an indirect or direct impact to products or patients, and they serve as the system of record for compliance. The way compliance is tracked must meet standards established by regulatory requirements, such as FDA 21 CFR Part 11 and EU Annex 11, which govern computerized systems and electronic records/signatures for regulated activities. (For more information on the history of FDA regulation in the U.S., click here.)
Anything considered to have “Good Practice” (GxP) compliance impact, such as training for lab technicians, will need to follow defined guidelines. If the requirements are not met, there could be severe consequences imposed by the government and industry regulatory bodies, including monetary fines or halting the manufacturing of products. As a result, each GxP change must go through a more rigorous vetting process, including documentation, impact analysis, testing in several environments, evidence of change success, and approvals at several stages. Anything that is not considered to have GxP impact, such as changing the text in an email notification, would not need to go through this strict process.
What is the risk?
The three main questions to ask yourself when evaluating a change for a validated LMS environment are:
1.) What is the probability of harm occurring due to the problem/issue and the proposed change?
2.) What is the severity of impact of the problem/issue and the proposed change?
3.) What is the visibility of the problem/issue and the proposed change?
The answers to these questions will determine the risk of the fix or update. A change considered high risk would likely require more detailed testing and verification compared to something classified as low risk. The difference could mean a lengthy test script compared to just a screenshot attachment.
How do you prioritize change requests?
An LMS is constantly evolving and being improved upon, so prioritizing requests helps keep the roadmap organized and moving forward. Change requests can be voluntarily initiated by anyone using the LMS, whether learners or administrators, or they may be necessary as a result of software updates. The reasoning behind the change request will be the most important factor in determining its priority and where it falls in the list of enhancements. For example, fixing a system issue or validating an upcoming software release will take the highest priority, whereas aesthetic changes to the home page or notifications will be low priority.
Who takes part in the change control process?
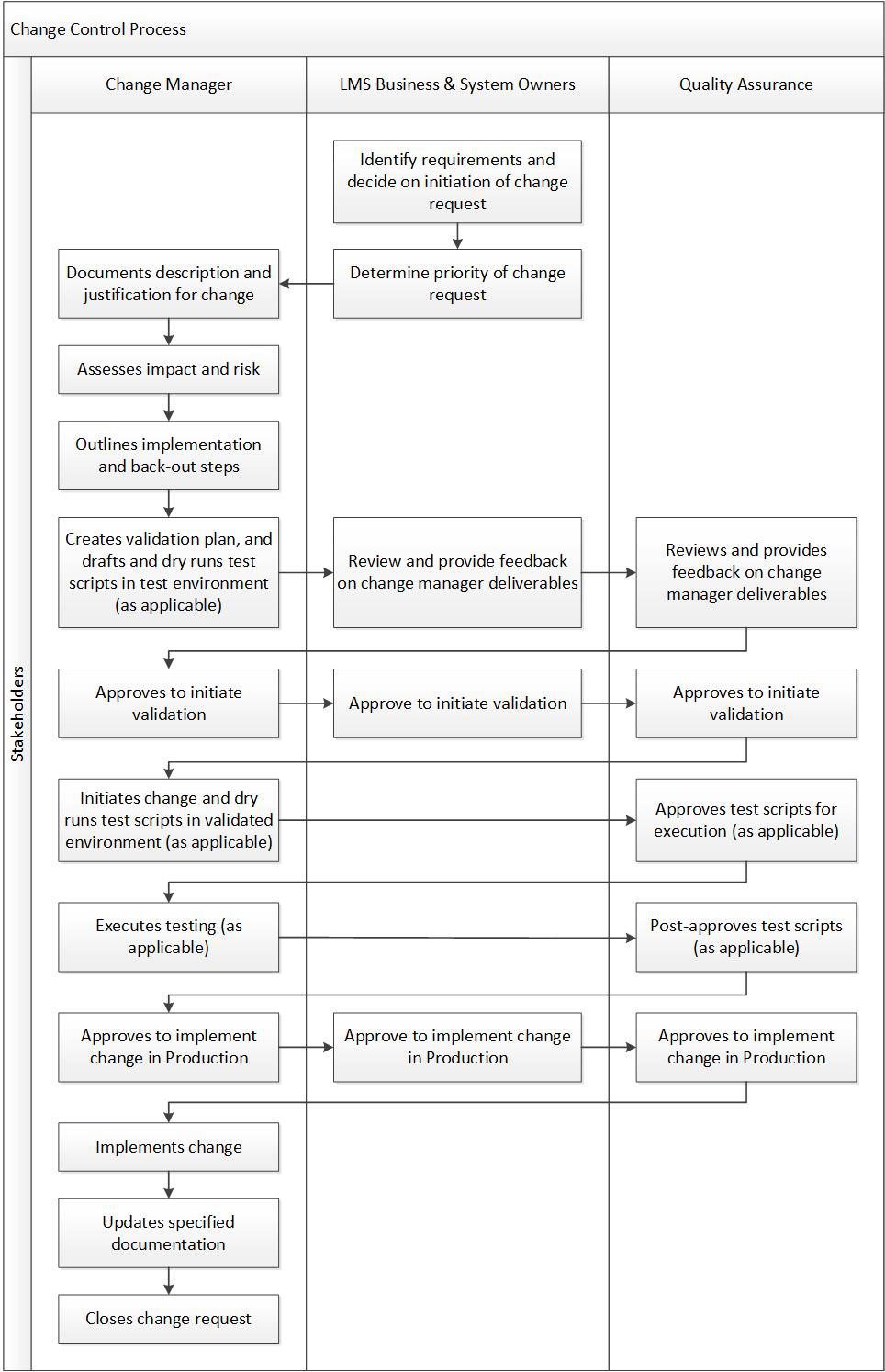
There should be several roles involved in the change control process, including the change manager, the LMS business and system owners, and the quality assurance team, to maintain proper system oversight. The change manager is responsible for driving the change request through the process from beginning to end, but it is a collaborative effort involving feedback from and coordination between all roles until the change is implemented in Production. The chart below outlines the main responsibilities of each role throughout the process workflow:
Now that we have covered the basics of change management in validated LMS environments, check out this post on best practices to follow.





